📋 Overview
Cybersecurity involves protecting computer systems, networks, and data from unauthorized access, theft, or damage. With the rise of digital technologies, cybersecurity has become a critical field, safeguarding personal information, corporate assets, and national security. RC passages on cybersecurity often address topics such as hacking techniques, ethical concerns, and the evolving landscape of cyber threats. Understanding these concepts equips readers to analyze the challenges and strategies associated with maintaining digital security.
🔑 Key Concepts
This guide will explore the following essential cybersecurity concepts:
- Definition and Importance of Cybersecurity
- Types of Cyber Threats
- Cryptography and Data Protection
- Cybersecurity Policies and Frameworks
- Ethical Hacking and Penetration Testing
- Role of Artificial Intelligence in Cybersecurity
- Cybersecurity in Critical Infrastructure
- Challenges in Cybersecurity
- Global Collaboration in Cybersecurity
- Future Trends in Cybersecurity
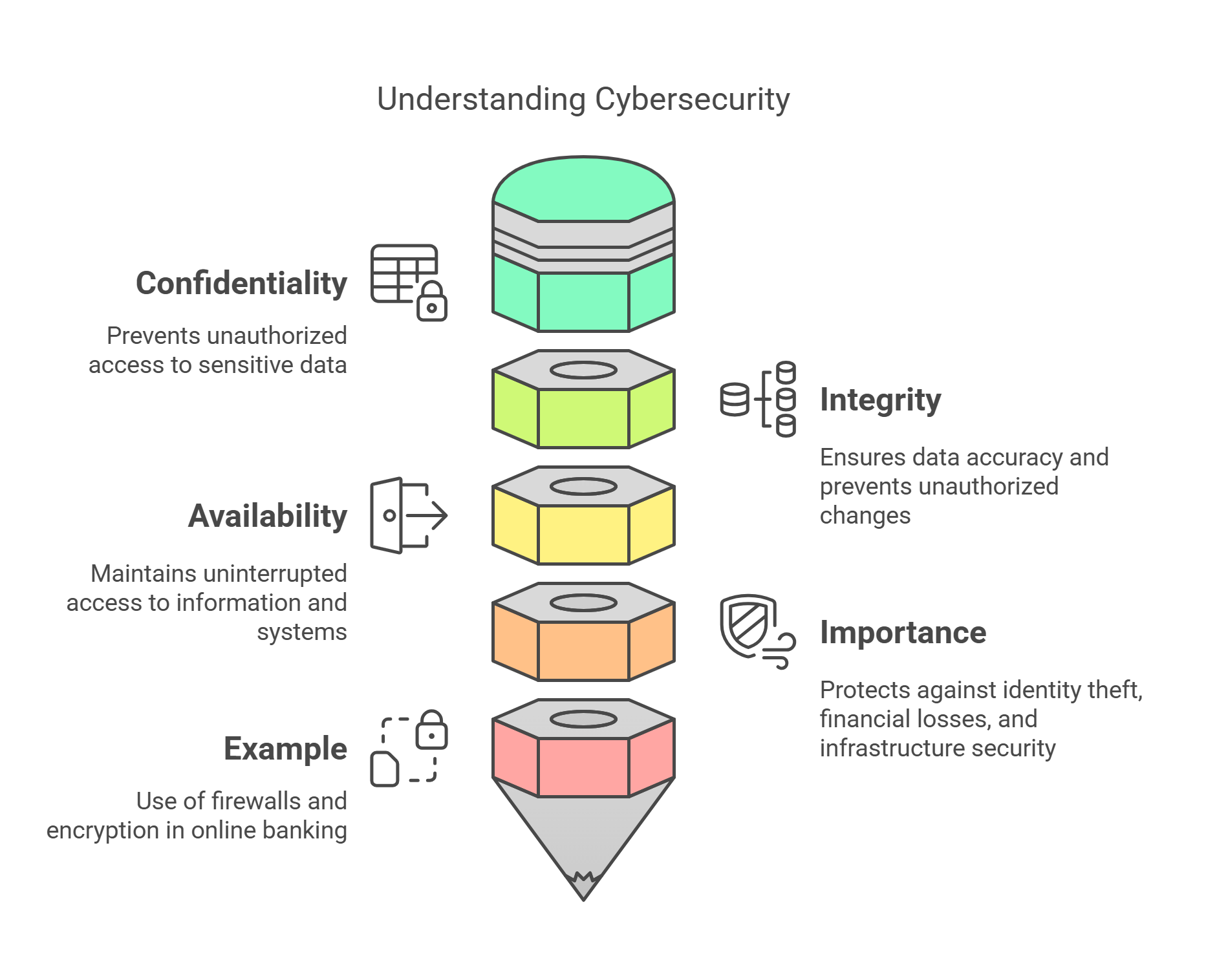
1. Definition and Importance of Cybersecurity
Cybersecurity refers to the practices, technologies, and processes designed to protect computer systems, networks, and data from cyberattacks. It ensures the confidentiality, integrity, and availability of digital information.
- Key Objectives:
- Confidentiality: Prevent unauthorized access to sensitive data.
- Integrity: Ensure data accuracy and prevent unauthorized modifications.
- Availability: Maintain uninterrupted access to information and systems.
- Importance:
- Protects individuals from identity theft.
- Safeguards businesses against financial losses and reputational damage.
- Ensures the security of critical infrastructure, such as power grids and healthcare systems.
- Example: Implementing firewalls and encryption to secure online banking transactions.
Explained Simply: Cybersecurity is like locking the doors and windows of your digital house to keep intruders out.
2. Types of Cyber Threats
Cyber threats encompass a wide range of malicious activities aimed at disrupting systems or stealing data. Understanding these threats is crucial for developing effective defense strategies.
- Common Threats:
- Phishing: Fraudulent emails or messages tricking users into revealing sensitive information.
- Malware: Malicious software, such as viruses, worms, and ransomware, designed to damage or control systems.
- Denial-of-Service (DoS) Attacks: Overwhelming a system with traffic to render it inoperable.
- Zero-Day Exploits: Attacks targeting vulnerabilities unknown to software developers.
- Examples:
- The WannaCry ransomware attack encrypted data on thousands of computers worldwide, demanding payment for decryption keys.
- Spear phishing campaigns targeting employees in organizations to gain unauthorized access to sensitive data.
Explained Simply: Cyber threats are like digital traps set by attackers to steal, disrupt, or damage valuable assets.
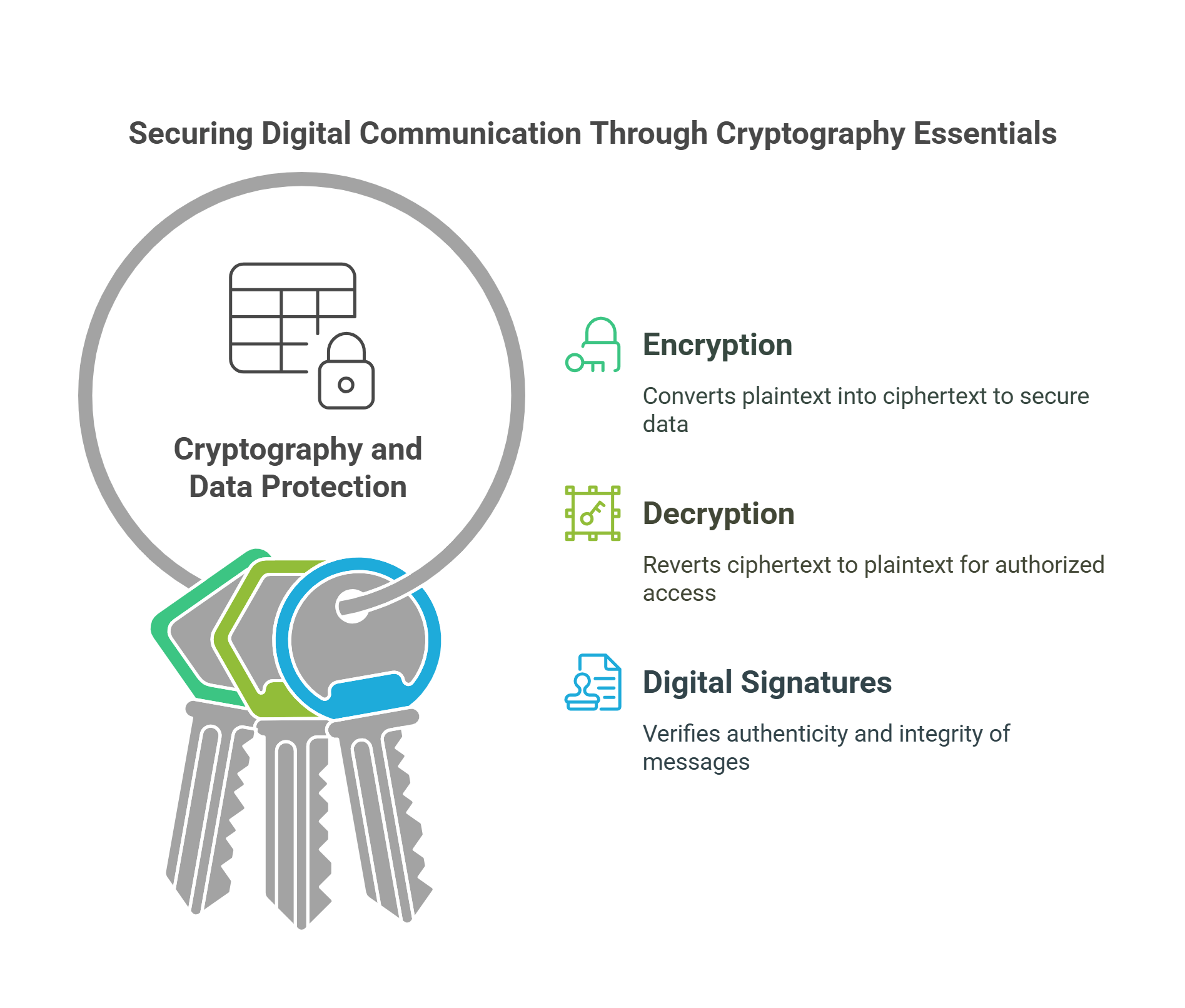
3. Cryptography and Data Protection
Cryptography secures communication and data by transforming information into unreadable formats, ensuring that only authorized parties can access it.
- Key Concepts:
- Encryption: Converts plaintext into ciphertext using algorithms and keys.
- Decryption: Reverts ciphertext back to plaintext for authorized users.
- Digital Signatures: Verify the authenticity and integrity of messages or documents.
- Applications:
- Secure online transactions (e.g., HTTPS protocols).
- Protecting sensitive data in storage and transmission.
- Example: End-to-end encryption in messaging apps like WhatsApp ensures that only the sender and receiver can read messages.
Explained Simply: Cryptography is like a secret code that keeps your digital messages and data safe from prying eyes.
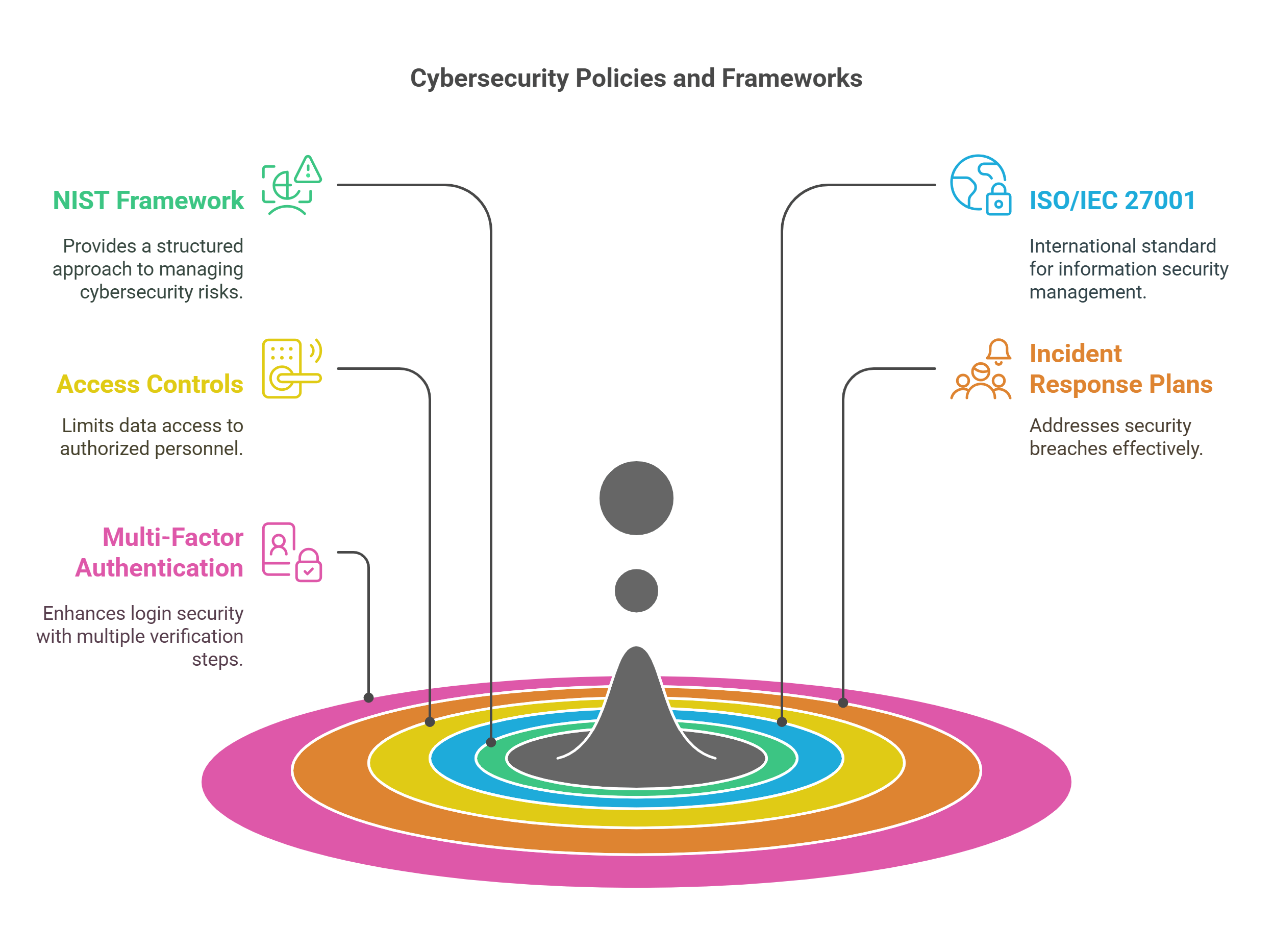
4. Cybersecurity Policies and Frameworks
Cybersecurity policies and frameworks establish guidelines and standards for protecting systems and data across organizations.
- Popular Frameworks:
- NIST Cybersecurity Framework: Provides a structured approach to managing and reducing cybersecurity risks.
- ISO/IEC 27001: International standard for information security management.
- Key Policies:
- Access controls to limit data access to authorized personnel.
- Incident response plans to address security breaches effectively.
- Example: A company implementing multi-factor authentication (MFA) to enhance login security.
Explained Simply: Cybersecurity frameworks are like rulebooks that help organizations stay safe in the digital world.
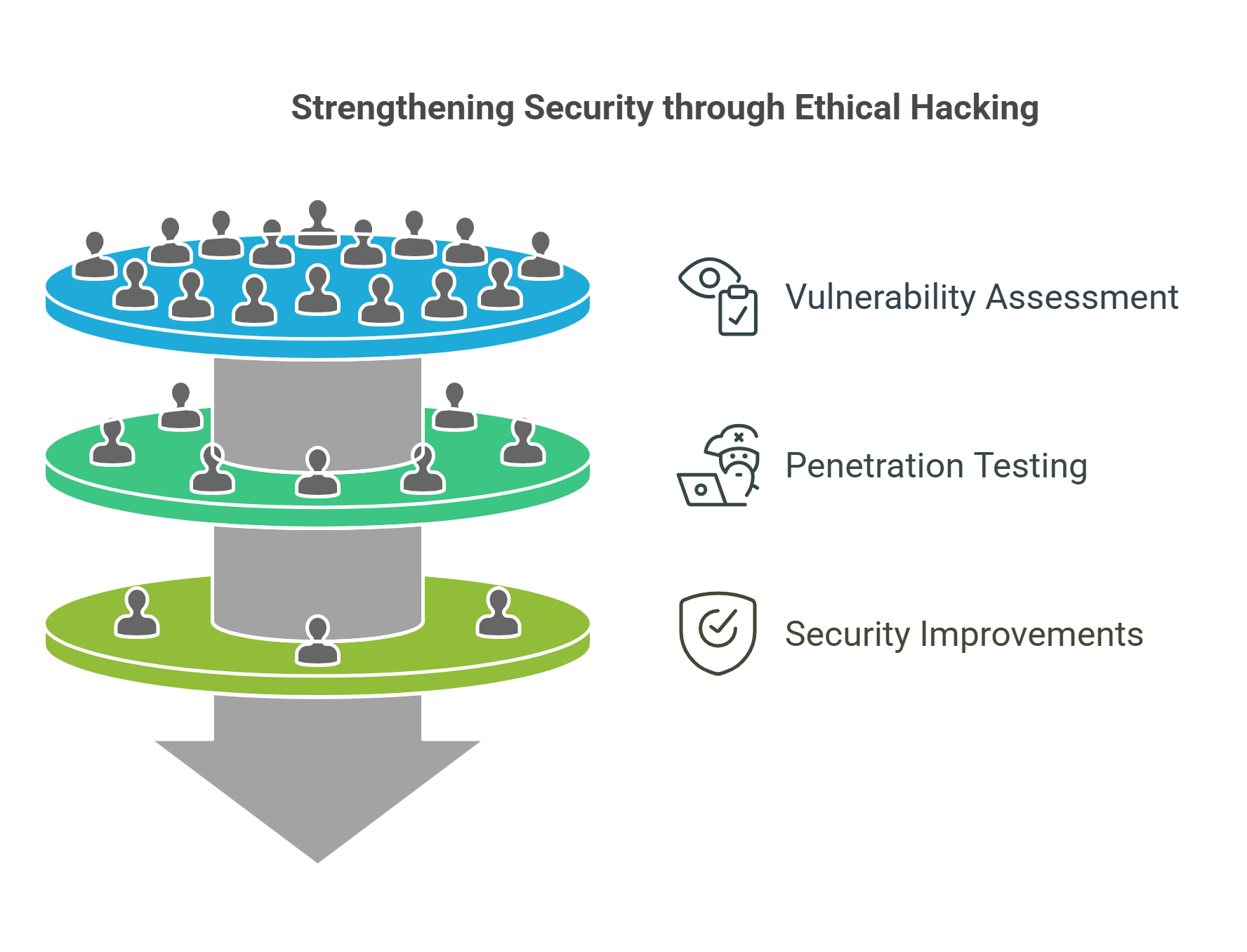
5. Ethical Hacking and Penetration Testing
Ethical hacking involves authorized attempts to identify vulnerabilities in systems and networks, helping organizations strengthen their defenses.
- Key Practices:
- Penetration Testing (Pen Testing): Simulates real-world attacks to find security gaps.
- Vulnerability Assessments: Systematic reviews of potential weaknesses.
- Examples:
- Ethical hackers testing a company’s website for exploitable flaws.
- Identifying weak passwords or outdated software as entry points for attackers.
- Impact: Improves security by addressing vulnerabilities before malicious hackers can exploit them.
Explained Simply: Ethical hacking is like hiring a professional to test your locks and security systems before burglars do.
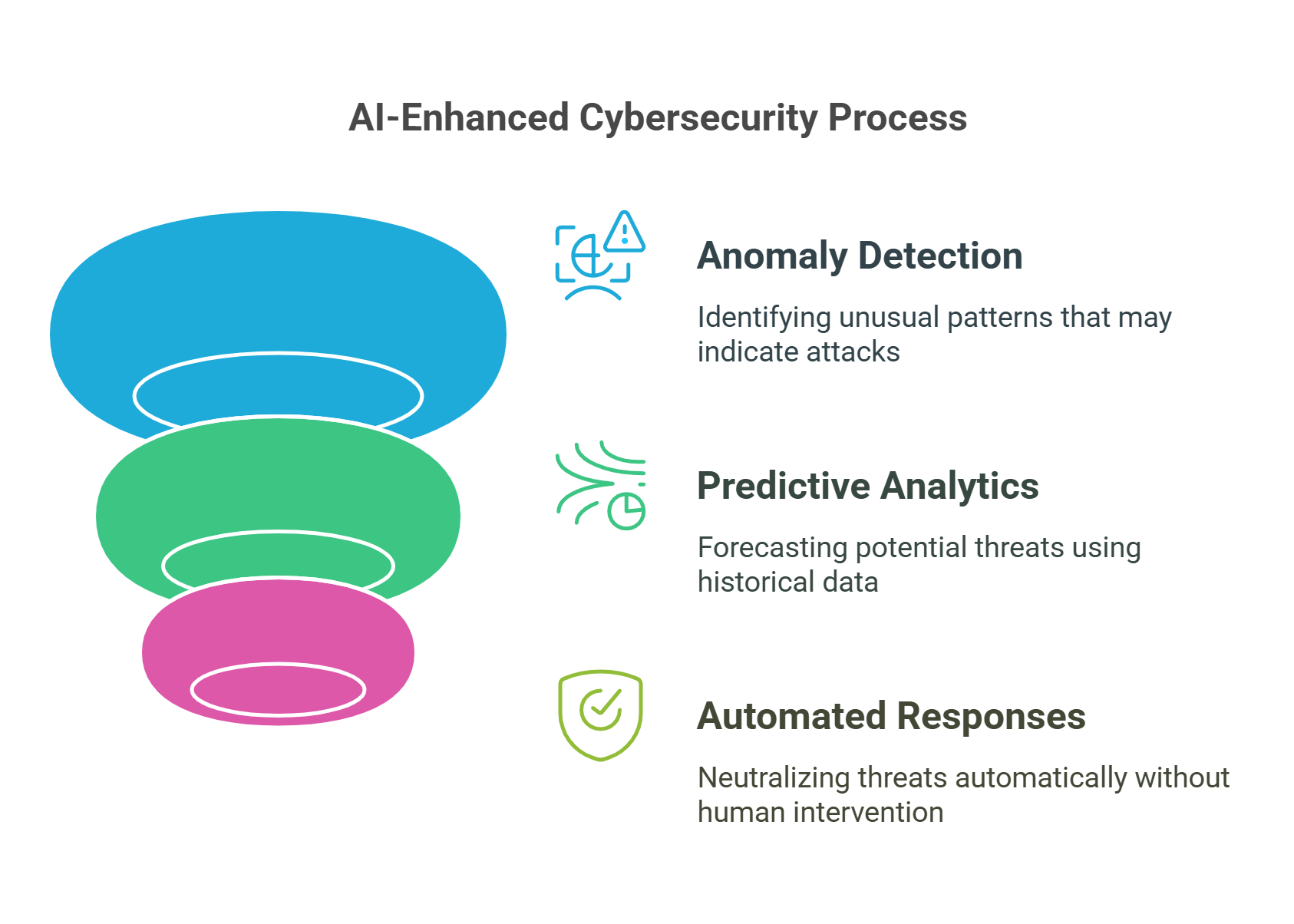
6. Role of Artificial Intelligence in Cybersecurity
Artificial intelligence (AI) enhances cybersecurity by automating threat detection, analysis, and response.
- Applications:
- Anomaly Detection: Identifies unusual patterns that may indicate a cyberattack.
- Predictive Analytics: Forecasts potential threats based on historical data.
- Automated Responses: AI-powered tools can neutralize threats without human intervention.
- Examples:
- AI systems detecting and blocking phishing emails.
- Using machine learning algorithms to identify malware signatures.
- Benefits: Speeds up response times, reduces human error, and adapts to evolving threats.
Explained Simply: AI in cybersecurity is like a guard dog that learns to detect new threats and acts quickly to protect you.
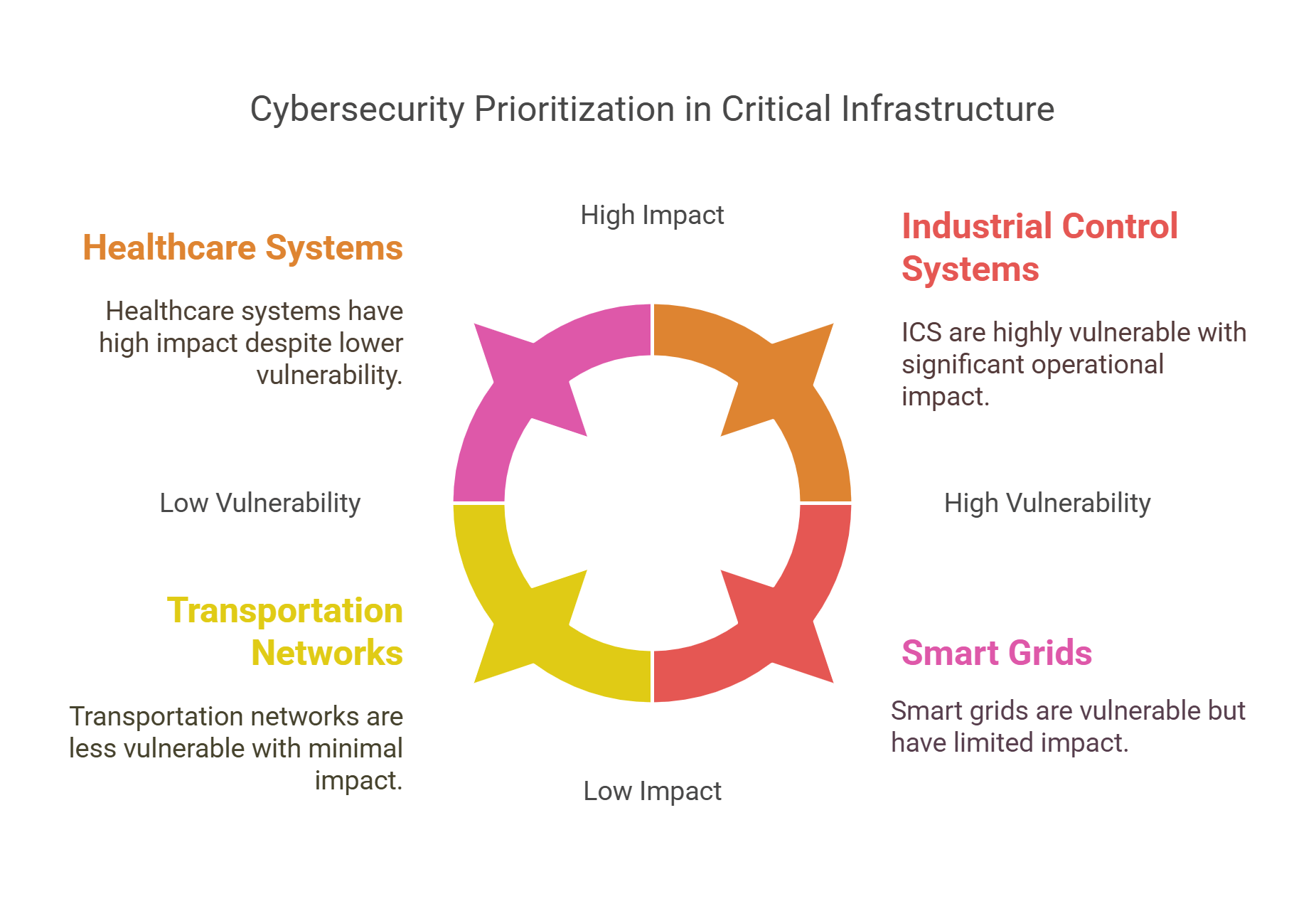
7. Cybersecurity in Critical Infrastructure
Critical infrastructure includes essential systems like power grids, water supply, healthcare facilities, and transportation networks. Cybersecurity ensures the protection of these systems from cyberattacks that could disrupt society.
- Key Concerns:
- Industrial Control Systems (ICS): Vulnerable to targeted attacks that disrupt operations.
- Healthcare Systems: Attacks on hospitals can jeopardize patient safety and data privacy.
- Examples:
- The 2021 Colonial Pipeline ransomware attack disrupted fuel supply across the U.S. East Coast.
- Cyberattacks on smart grids aiming to cut off electricity.
- Impact: Protecting critical infrastructure is vital for national security and public safety.
Explained Simply: Cybersecurity for critical infrastructure is like safeguarding the backbone of society against digital threats.
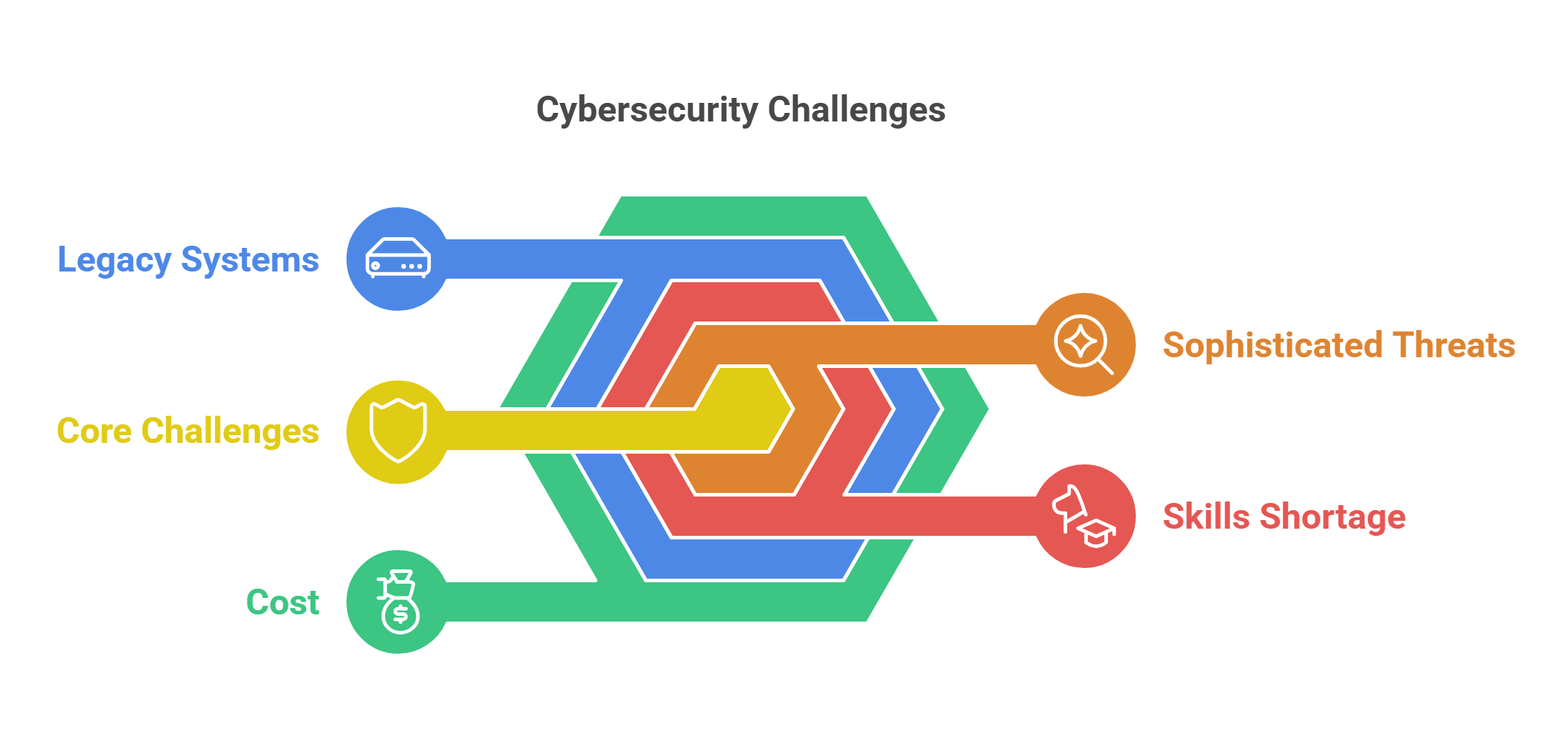
8. Challenges in Cybersecurity
The rapidly evolving nature of technology presents numerous challenges for cybersecurity professionals.
- Key Challenges:
- Sophisticated Threats: Attackers use advanced techniques like AI and deepfake technology.
- Skills Shortage: Lack of trained cybersecurity professionals to meet growing demand.
- Legacy Systems: Older systems often lack modern security features.
- Cost: High costs associated with implementing robust cybersecurity measures.
- Examples:
- Small businesses struggling to afford cybersecurity tools.
- Organizations facing ransomware attacks due to outdated systems.
Explained Simply: Cybersecurity faces constant battles with new threats, limited resources, and outdated systems.
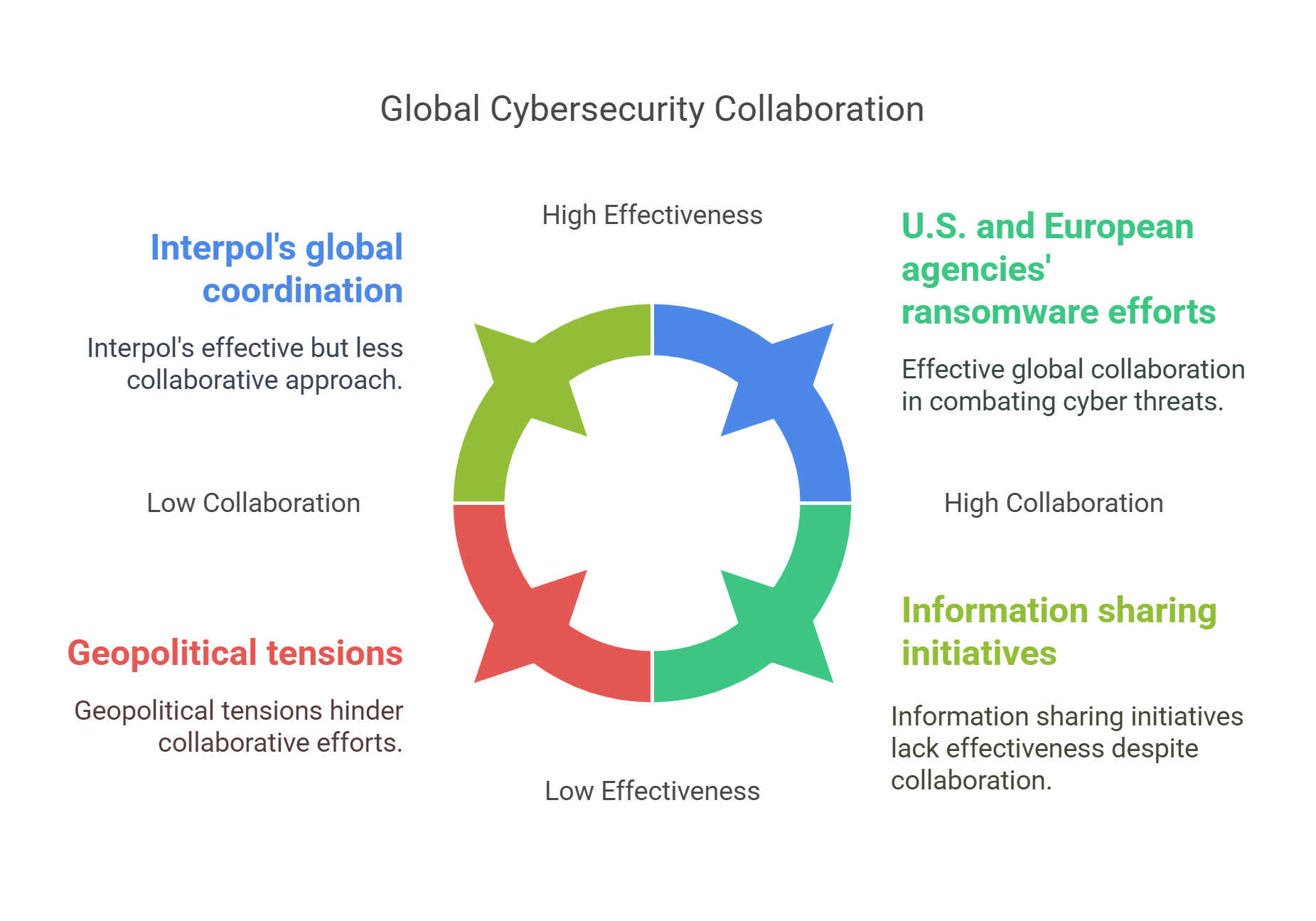
9. Global Collaboration in Cybersecurity
Cyber threats often cross national borders, requiring global cooperation to address them effectively.
- International Efforts:
- Budapest Convention on Cybercrime: International treaty aimed at combating cybercrime.
- Interpol’s Cybercrime Directorate: Coordinates efforts to tackle cybercrime globally.
- Information Sharing: Countries and organizations share threat intelligence to improve collective defenses.
- Challenges:
- Differences in legal frameworks and priorities between nations.
- Geopolitical tensions hindering cooperation.
- Example: Collaboration between U.S. and European agencies to dismantle global ransomware networks.
Explained Simply: Global collaboration is like a neighborhood watch program for the digital world, where countries work together to stop cybercriminals.
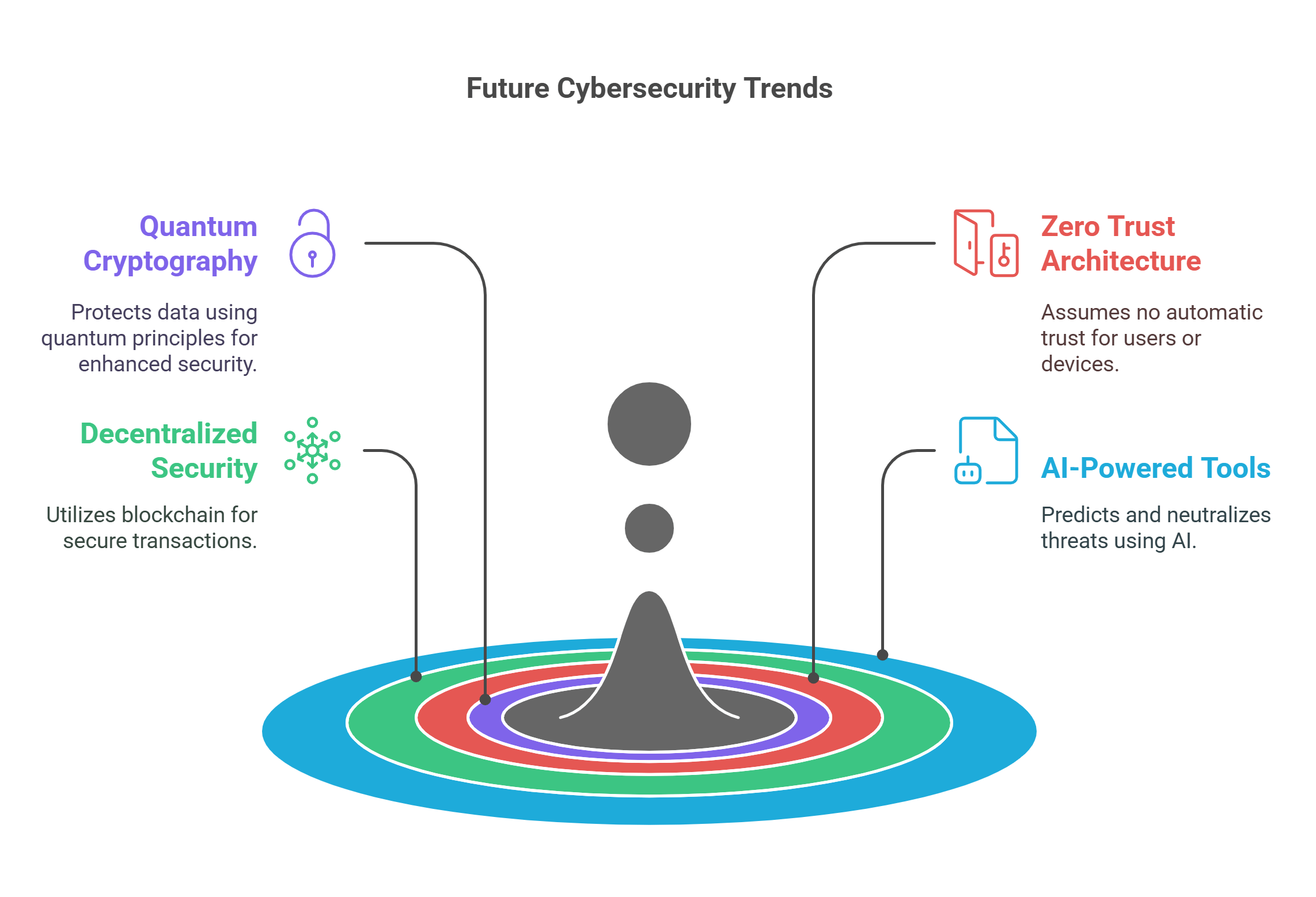
10. Future Trends in Cybersecurity
The future of cybersecurity is shaped by advancements in technology and the emergence of new threats. Staying ahead requires innovation and adaptability.
- Trends:
- Quantum Cryptography: Protects data using quantum computing principles.
- Zero Trust Architecture: Assumes no user or device is automatically trusted.
- Decentralized Security: Blockchain-based solutions for secure transactions.
- Challenges:
- Balancing security with user convenience.
- Addressing privacy concerns in an era of increasing surveillance.
- Example: Emerging AI-powered cybersecurity tools that predict and neutralize threats before they occur.
Explained Simply: Future cybersecurity trends are like upgrading your tools to tackle increasingly sophisticated digital threats.
✨ Conclusion
Cybersecurity is an ever-evolving field that plays a crucial role in safeguarding the digital world. By mastering concepts like cryptography, AI applications, and global collaboration, readers can better analyze RC passages on this vital topic. Understanding cybersecurity equips us to navigate the complexities of the digital age and protect critical systems, data, and privacy. 🔒












